Bitcoin technology primer
It can take many years to understand bitcoin in every detail, but luckily you don’t need to know everything to design great products. Let’s take a look at the most important ideas and technologies behind Bitcoin by answering some basic questions.
Is it Bitcoin or bitcoin?

It’s both. Lowercase bitcoin refers to the currency. So you may have 1 bitcoin in your wallet. Capitalized Bitcoin refers to the protocol and payment network.
What is a bitcoin?

Bitcoin (as in “I have 1 bitcoin”) are just numbers in the database of transactions often referred to as the bitcoin block chain.
A transaction involves sending bitcoin from one address to another. This reduces the available balance of the sending address, and increases the balance of the receiving address. A small amount is deducted to pay for the transaction fee.
Owning a bitcoin therefore means being in control of one or more addresses that have received bitcoin.
How do I get an address?
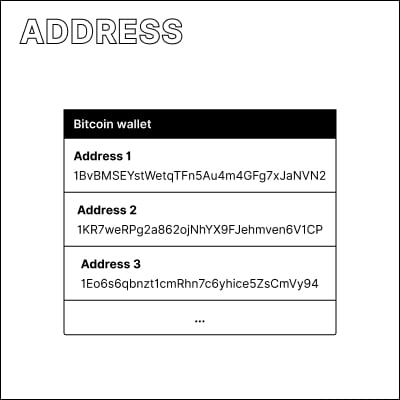
Bitcoin wallet software can generate as many addresses as you need. Note that addresses are generated on your own computer. They follow a specific format, but there is no centralized system to verify or approve them. Valid addresses can even be generated on computers that have never been online.
It is best practice to use a new address for every transaction. The Bitcoin network does not store why transactions were made, so it is common to use addresses as invoice IDs or payment IDs. As transaction data is public and can be analyzed, using many different addresses also provides privacy benefits by making it harder to trace how you receive and spend bitcoin.
What’s my balance?
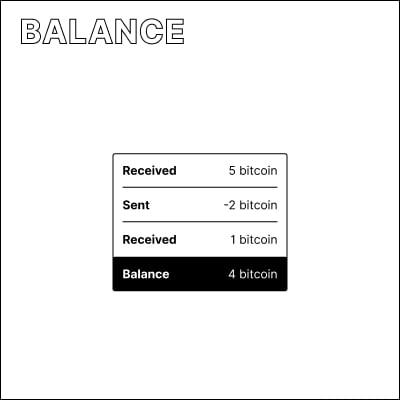
The Bitcoin network does not store your balance. This value is dynamically calculated by summing up all bitcoin you have received on your addresses, and subtracting bitcoin you spent.
To do this, a wallet application needs to know your full transaction history in order to calculate how much bitcoin you have.
Do I need to remember all my addresses?
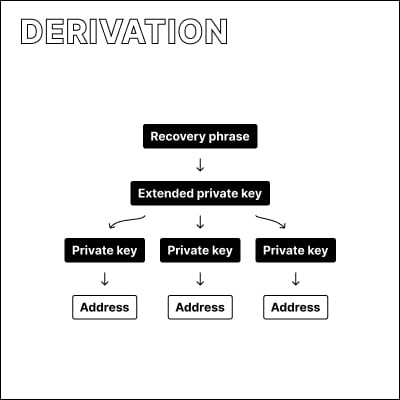
No. Most wallets generate them using a standard called Hierarchical Deterministic Wallets. All your addresses and private keys are derived from a single piece of information, called the recovery phrase.
This makes backing up your wallet fairly easy, as you only need to securely store your recovery phrase to restore your wallet. However, it also concentrates the risk of having your bitcoin stolen or lost to this one piece of information. Because of this, supporting and guiding users in backing up and securing their wallets is one of the most fundamental goals for designers.
How do you control an address?

As we now know, bitcoin are just numbers linked to addresses. An address can receive bitcoin, but in oder to spend those bitcoin, a private key is needed. Wallets actually create private keys first, and then derive matching addresses from them. While an address can be publicly shared, the private key should be kept a secret.
Wallet software typically hides private keys from users, as there is no need to interact with them directly.
How are private keys and addresses connected?
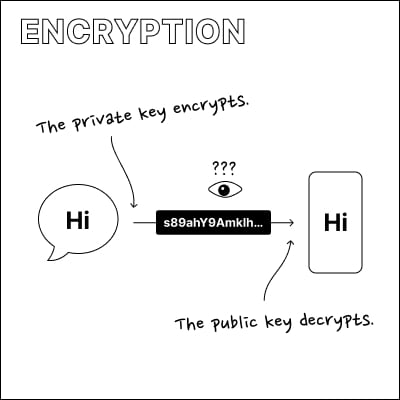
A private key is used to scramble information. The matching public key (which we call an address in Bitcoin) can unscramble the information again. This allows for the transfer of information without any third party being able to understand it.
Note that there is a strong element of identity in this mechanism, as it ensures that only the recipient can unscramble the message while also being able to verify that the message actually came from the expected sender. This requires that both parties securely exchange public keys with each other in a secure way.
More info
Signature

Since a private key can be used to prove that the holder controls a specific address, it can therefore authorize transactions from the address. This is called a digital signature.
One of the most important activities of the Bitcoin network is to verify that signatures are valid.
So are all my transactions encrypted?

No. Transactions are stored in a plain format in the Bitcoin network for anyone with an internet connection to see and analyze. This allows for observers to verify that all transactions in the system are valid and that nobody spends bitcoin they don’t have. This transparency is unique to Bitcoin compared to any other traditional currency. At the same time it introduces potential privacy problems.
More info
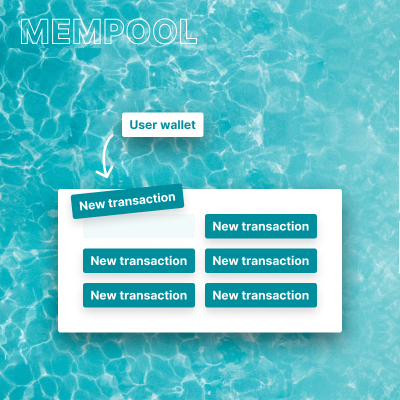
How are transactions processed?
Texture by Emilio Garcia on Unsplash.
Every transaction needs to be confirmed before the recipient can consider the involved bitcoin theirs. This waiting line for new transactions is called the mempool. The Bitcoin network can only process a certain amount of transactions per day, so it may take longer to process your transactions during busy times. Transactions that involve higher fees are typically processed faster.
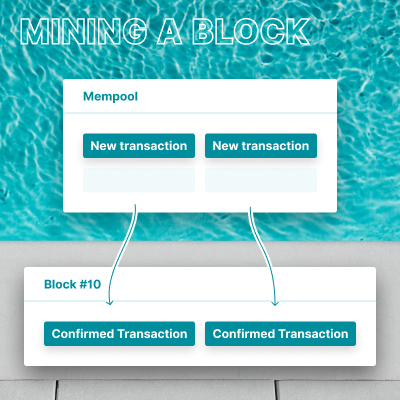
How are transactions confirmed?
Texture by Thom Milkovic on Unsplash.
This function is performed by miners, which are computers that group new transactions from the mempool into blocks and try to get those blocks accepted by the Bitcoin network. They are called miners because the creation of new blocks is rewarded by freshly minted bitcoin. This is the only way bitcoin are created, which creates heavy competition around mining.
Once a transaction is in a block that has been accepted by the network, it is considered as having one confirmation. With every new block created, the number of confirmations of this particular block increases.
More info
What is a block?
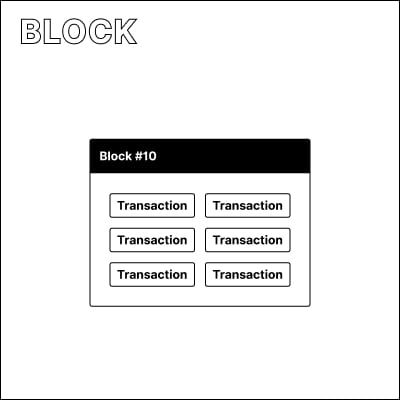
Instead of processing each transaction individually, the Bitcoin network bundles them into blocks. Blocks are created roughly every 10 minutes, and can only contain a certain amount of transactions due to a strict file size limit. Once a block is accepted and has several confirmations, it can never be changed again.
What makes it a block chain?
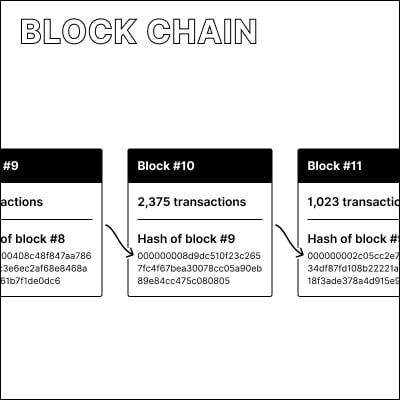
This term refers to the linking of blocks by embedding a hash (a digital fingerprint) of one block into the next one. This allows for verifying that new blocks are based on the same history of blocks that nodes in the Bitcoin network have already agreed upon.
What is a hash?

Example of a SHA-256 hash.
Another fundamental technique to cryptography and Bitcoin is called hashing. It is the process of taking data and applying a function that creates a unique identifier for it. This is called a hash and can be thought of as a fingerprint.
Unlike encryption, a hash does not contain the original data and the hashing process cannot be reversed. Since hashes are small in size, they are a great way to verify the authenticity of information.
What is a node?
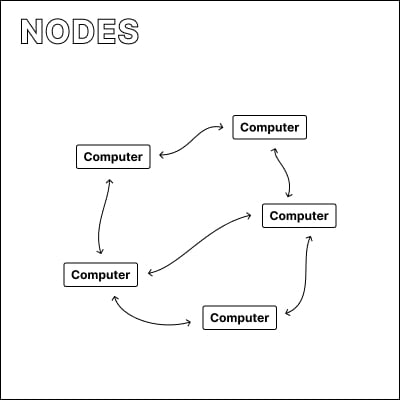
While miners create blocks, nodes verify, distribute and store blocks. Just like miners, nodes are computers communicating with each other, constantly exchanging information to ensure that the rules of the Bitcoin protocol are adhered to.
With thousands of nodes all over the world, operated by many different people, it becomes almost impossible to manipulate data this network has agreed upon. It would require at least half of these nodes to collude.
More info
There’s a lot more
These are some of the basic technological concepts that make Bitcoin work. Each one individually is complex, and the interplay between them is a whole other area of interest. Dive into the other chapters in this guide to explore the technnology and its applications in more detail.

Now, if you’d like to go all the way to the beginning of Bitcoin, the most fundamental read is the Bitcoin whitepaper. Published on October 31, 2008 by the mysterious Satoshi Nakamoto, it lays out the fundamental system design in only 9 short pages. It is not necessarily an easy read, but still highly recommended reading.
Take a look at how these technologies are implemented in the various types of bitcoin software.